Parameter¶
The CEP is highly customizable. This can be done by changing parameters of the CEP via environment variables configured in a docker-compose.yml file.
Available Parameters¶
CEP_AAF_ALLOW_REGISTRATION¶
If true registration via EMAIL_OTP:1 will be allowed. If the method EMAIL_OTP:1 is not available the user get the message configured in AA for this purpose.
Logins with single method
For security reasons, there should be a chain available for the user which includes EMAIL_OTP:1 + X. X stands for a method each user has to enroll the on his first login. That makes the E-Mail OTP only chain unavailable after the enrollment of his first methods like PASSWORD:1. Next time he tries to login, the user has to use at least PASSWORD:1 + EMAIL_OTP:1. Registration become also unavailable for the user if he has at least PASSWORD:1 + EMAIL_OTP:1 enrolled. It's recommended adding this first minimal method to the CEP_AAF_UNDELETEABLE_METHODS parameter as well. To have a backup for the user to reset his PIN there should also be a chain available including 2 methods + EMAIL_OTP:1. The two other methods should not be something the user has to remember.
environment:
- CEP_AAF_ALLOW_REGISTRATION=true
environment:
- CEP_AAF_ALLOW_REGISTRATION=false
CEP_AAF_ALLOW_REGISTRATION_METHODS¶
If one of these methods available in a chain to authenticate for "Authenticators Management", registration will be denied for the user.
environment:
- CEP_AAF_ALLOW_REGISTRATION=["PASSWORD:1"]
environment:
- CEP_AAF_ALLOW_REGISTRATION=[]
CEP_AAF_ALLOWED_USERGROUPS¶
Array of groups DN's allowed to log into the CEP. If not defined all groups are allowed.
environment:
- CEP_AAF_ALLOWED_USERGROUPS=["CN=AAF-User,OU=AAF,OU=AUTH,DC=COMPANY,DC=DE"]
environment:
- CEP_AAF_ALLOWED_USERGROUPS=[]
CEP_AAF_ENDPOINT_ID¶
The unique ID of the endpoint created in the AAF.
yaml title="Example"
environment:
- CEP_AAF_ENDPOINT_ID=269ee2864b1f12edab980242ac124563
environment:
- CEP_AAF_ENDPOINT_ID=xxxxxxxxx
CEP_AAF_ENDPOINT_SECRET¶
The endpoint secret of the corresponding endpoint in the AAF backend.
environment:
- CEP_AAF_ENDPOINT_SECRET=XRuLj2sOdBrsP2lYUZCdskQedN6xUiFt
environment:
- CEP_AAF_ENDPOINT_SECRET=xxxxxxxxx
CEP_AAF_ENDPOINT_URL¶
URL of the AAF webserver.
environment:
- CEP_AAF_ENDPOINT_URL=https://aaf.mtrix.com
environment:
- CEP_AAF_ENDPOINT_URL=
Internal Certificate Authorities
It's very important to consider possible internal CAs. If communication with the AAF is not possible, internal Certificate Authority must be added to the custom cep container.
CEP_AAF_EXPOSE_NOCHAIN¶
If true user will see an error message that no chains is available. If registration is enabled, the message will guide the user to use registration.
environment:
- CEP_AAF_EXPOSE_NOCHAIN=true
environment:
- CEP_AAF_EXPOSE_NOCHAIN=false
CEP_AAF_HIDDEN_LOGIN_METHODS¶
All chains containing one of the configured hidden methods will not be displayed on the normal login. They will be accepted for method reset and registration.
environment:
- CEP_AAF_HIDDEN_LOGIN_METHODS=["EMAIL_OTP:1"]
environment:
- CEP_AAF_HIDDEN_LOGIN_METHODS=[]
CEP_AAF_LOGIN_EVENT¶
Optional login event that allows authenticators to be managed. Only 'Authenticators Management' is supported.
environment:
- CEP_AAF_LOGIN_EVENT=Authenticators Management
environment:
- CEP_AAF_LOGIN_EVENT=Authenticators Management
CEP_AAF_LOGIN_METHODS¶
YAML array of the methods offered to the user by the portal login. If not set all methods configured for the Authenticators Management and chains will be useable.
environment:
- CEP_AAF_LOGIN_METHODS=["PASSWORD:1", "TOTP:1", "EMERG_PASSWORD:1", "SMARTPHONE:1", "HOTP:1", "U2F:1", "SECQUEST:1", "CARD:1", "FIDO2:1", "FINGER:1", "LDAP_PASSWORD:1", "WINHELLO:1", "SMARTPHONE:1", "BLUETOOTH:1"]
environment:
- CEP_AAF_LOGIN_METHODS=[]
CEP_AAF_LOGON_USER_REGEX¶
A regular expression all usernames must match with. If the username does not match the user get Invalid Credentials as error message.
Before the check repository name will be removed from user input.
environment:
- CEP_AAF_LOGON_USER_REGEX=/^test[0-9]*$$/i
environment:
- CEP_AAF_LOGON_USER_REGEX=/^.*$$/i
CEP_AAF_METHODS¶
YAML array of the methods offered to the user by the portal.
environment:
- CEP_AAF_METHODS=["PASSWORD:1", "TOTP:1", "EMERG_PASSWORD:1", "SMARTPHONE:1", "HOTP:1", "U2F:1", "SECQUEST:1", "CARD:1", "FIDO2:1", "FINGER:1", "LDAP_PASSWORD:1", "WINHELLO:1", "SMARTPHONE:1", "BLUETOOTH:1"]
CEP_AAF_METHODS_USER_REGEX¶
YAML array to limit method access for specific users.
This example demonstrates how to restrict the methods LDAP PASSWORD:1 and FIDO2:1 for usernames like test12345. All other methods are allowed by regular expression matching all usernames. There is no additional restriction to an authentication method by this feature If the method is not configured here.
environment:
- CEP_AAF_METHODS=["LDAP_PASSWORD:1", "FIDO2:1", "PASSWORD:1", "SMARTPHONE:1", "HOTP:1", "SMARTPHONE:1"]
- 'CEP_AAF_METHODS_USER_REGEX={"LDAP_PASSWORD:1" : "/^test[0-9]*$$/i", "FIDO2:1" : "/^test[0-9]*$$/i", "PASSWORD:1" : "/^.*$$/i", "SMARTPHONE:1" : "/^.*$$/i", "HOTP:1" : "/^.*$$/i", "SMARTPHONE:1" : "/^.*$$/i"}'
Default settings do not restrict any an extra limitation to authentication methods.
environment:
- CEP_AAF_METHODS_USER_REGEX=[]
CEP_AAF_MULTI_METHODS¶
Array with methods that can be registered multiple times by users, if categories are configured and available for the user.
environment:
- CEP_AAF_MULTI_METHODS=["TOTP:1", "HOTP:1", "U2F:1"]
environment:
- CEP_AAF_MULTI_METHODS=[]
CEP_AAF_REGISTRATION_RESPECT_ORDER¶
If this parameter is set to false CEP will force prioritization by CEP_SINGLE_ALLOWD_METHOD.
environment:
- CEP_AAF_REGISTRATION_RESPECT_ORDER=false
environment:
- CEP_AAF_REGISTRATION_RESPECT_ORDER=true
CEP_AAF_RESET_METHOD¶
If configured with a method like password, it will enable the authenticator reset functionality. With this functionality, the CEP looks for an alternative chains, which does not require configured reset method as an authentication factor. If found the user can login with this chain normally. If no chains is available, then the user see and error message. After the user logged in successfully, he will be redirected to the configured method (template) to modify it.
environment:
- CEP_AAF_RESET_METHOD=PASSWORD:1
environment:
- CEP_AAF_RESET_METHOD=
CEP_AAF_TEST_EVENT¶
Individual event that is used to test the methods. This event must contain all the methods or chains that are relevant for the authentication of the methods configured with CEP_AAF_METHODS. This event must be created first before the users can test their methods in the CEP.
environment:
- CEP_AAF_TEST_EVENT=MethodTest
CEP_AAF_TRUSTED_HOSTS¶
This parameter allows configuring the matching hosts exclusively from the host header of the HTTP request. Any $ signs must be masked using a leading $.
environment:
- CEP_AAF_TRUSTED_HOSTS=^example\.com$$,^example\.org$$
environment:
- CEP_AAF_TRUSTED_HOSTS=
CEP_AAF_TRUSTED_PROXIES¶
A comma-separated list of all trusted upstream proxy ip addresses. CIDR notations are supported.
environment:
- CEP_AAF_TRUSTED_PROXIES=192.168.1.0/24,172.16.16.1
environment:
- CEP_AAF_TRUSTED_PROXIES=
CEP_AAF_UNDELETEABLE_METHODS¶
YAML array of the methods which can't be deleted by the user.
environment:
- CEP_AAF_UNDELETEABLE_METHODS=["PASSWORD:1", "EMAIL_OTP:1"]
environment:
- CEP_AAF_UNDELETEABLE_METHODS=[]
CEP_AAF_USECASES¶
Array with use cases:
environment:
- 'CEP_AAF_USECASES={"VPN": [["PASSWORD:1", "HOTP:1"], ["PASSWORD:1", "SMARTPHONE:1"]], "WINDOWS": [["PASSWORD:1", "U2F:1"], ["PASSWORD:1", "SMARTPHONE:1"]]}'
environment:
- CEP_AAF_USECASES=[]
CEP_AAF_USECASES_GROUP_LIMIT¶
Limit the visibility of use cases to specific user groups.
environment:
- 'CEP_AAF_USECASES_GROUP_LIMIT={"VPN": ["CN=VPN,CN=Users,DC=cep,DC=corp"], "BankingApp": ["CN=Finance,CN=Users,DC=cep,DC=corp"]}'
environment:
- CEP_AAF_USECASES_GROUP_LIMIT=[]
CEP_AAF_VERIFYPEER¶
If false, the AAF's SSL certificate is not checked.
Security Risk
DO NEVER EVER USE THIS ENV IN PRODUCTION ENVIRONMENTS.
environment:
- CEP_AAF_VERIFYPEER=false
environment:
- CEP_AAF_VERIFYPEER=true
CEP_AAF_WEBHOOK_DELAY¶
Delay in seconds to the process the webhook request
environment:
- CEP_AAF_WEBHOOK_DELAY=5
environment:
- CEP_AAF_WEBHOOK_DELAY=0
CEP_AAF_WEBHOOK_ENROLL_ROLLBACK¶
If the webhook does not return the configured HTTP code and CEP_AAF_WEBHOOK_ENROLL_ROLLBACK is true, the authentication template is deleted again immediately after registration.
environment:
- CEP_AAF_WEBHOOK_ENROLL_ROLLBACK=true
environment:
- CEP_AAF_WEBHOOK_ENROLL_ROLLBACK=false
CEP_AAF_WEBHOOK_EXPECTED_CODE¶
Expected HTTP code of the webhook request
environment:
- CEP_AAF_WEBHOOK_EXPECTED_CODE=203
environment:
- CEP_AAF_WEBHOOK_EXPECTED_CODE=200
CEP_AAF_WEBHOOK_IGNORE_ERROR¶
If true errors of the webhook will be ignored.
environment:
- CEP_AAF_WEBHOOK_IGNORE_ERROR=false
environment:
- CEP_AAF_WEBHOOK_IGNORE_ERROR=true
CEP_AAF_WEBHOOK_METHOD¶
HTTP method with which the webhook request is made.
environment:
- CEP_AAF_WEBHOOK_METHOD=GET
environment:
- CEP_AAF_WEBHOOK_METHOD=POST
CEP_AAF_WEBHOOK_PASSWORD¶
Webhook password for basic authentication
environment:
- CEP_AAF_WEBHOOK_PASSWORD=SecretPassw0rd
environment:
- CEP_AAF_WEBHOOK_PASSWORD=
CEP_AAF_WEBHOOK_URL¶
Webhook URL that is accessed using the configured HTTP method when a new method is used.
Placeholder for URL parameters are: ##METHOD##, ##USER##, ##ACTION##
environment:
- CEP_AAF_WEBHOOK_URL=http://example.com/##ACTION##/app/##METHOD##?user=##USER##
environment:
- CEP_AAF_WEBHOOK_URL=
CEP_AAF_WEBHOOK_USER_REPO¶
If true, the repository name (repo / username) is also stored in the user field
environment:
- CEP_AAF_WEBHOOK_USER_REPO=true
environment:
- CEP_AAF_WEBHOOK_USER_REPO=false
CEP_AAF_WEBHOOK_USERNAME¶
Webhook username for basic authentication
environment:
- CEP_AAF_WEBHOOK_USERNAME=username
environment:
- CEP_AAF_WEBHOOK_USERNAME=
CEP_AAF_WIZARD_DEFAULT_METHODS¶
This optional parameter based on a YAML array. It enables a default setting to be set for all repositories that have not been explicitly configured in the CEP_AAF_WIZARD_METHODS for a repository-based setting.
environment:
- CEP_AAF_WIZARD_DEFAULT_METHODS=["PASSWORD:1", "HOTP:1"]
environment:
- CEP_AAF_WIZARD_DEFAULT_METHODS=[]
CEP_AAF_WIZARD_METHODS¶
YAML array of methods that the user should confess to a wizard.
environment:
- CEP_AAF_WIZARD_METHODS=["PASSWORD:1", "HOTP:1", "SMARTPHONE:1", "CARD:1"]
environment:
- CEP_AAF_WIZARD_METHODS=[]
It is also possible to control a behavior of the wizard based on the user's repository.
environment:
- 'CEP_AAF_WIZARD_METHODS={"repo1": ["PASSWORD:1"], "repo2": ["PASSWORD:1", "HOTP:1"], "repo3": ["PASSWORD:1", "SMARTPHONE:1"]}'
Note
In this case, the single quotes are decisive so that the environment variable can be set correctly. If CEP_AAF_WIZARD_METHODS is configured, it is absolutely necessary to configure CEP_AAF_WIZARD_REPO_METHOD to true.
CEP_AAF_WIZARD_REPO_METHOD¶
Boolean value that specifies whether a wizard registration configured for the user's repository should be carried out.
environment:
- CEP_AAF_WIZARD_REPO_METHOD=true
environment:
- CEP_AAF_WIZARD_REPO_METHOD=false
CEP_ALLOWED_FIRST_TIME_METHODS¶
If CEP_ENABLE_FIRST_TIME_MESSAGE=true then the CEP looks for these methods. If only method configured with this parameter are enrolled by the user the first time user message will be displayed.
environment:
- CEP_ALLOWED_FIRST_TIME_METHODS=["LDAP_PASSWORD:1"]
environment:
- CEP_ALLOWED_FIRST_TIME_METHODS=[]
CEP_BASICAUTH_DEFAULT_METHOD¶
The CEP supports standard HTTP authorization with username and password. It is necessary to define the default method to use for the given password.
environment:
- CEP_BASICAUTH_DEFAULT_METHOD=PASSWORD:1
environment:
- CEP_BASICAUTH_DEFAULT_METHOD=LDAP_PASSWORD:1
CEP_BASICAUTH_ENABLE¶
If enabled the CEP will accept basic authentication header as source of username, method and secret for single sign-on authentication. Basic auth is allowed for LDAP_PASSWORD:1, PASSWORD:1 and EMERG_PASSWORD:1 method. If another method is required to complete a chain of authenticators management event, the user will be redirected to provide all required methods of one of the configured chain, including the already completed password method from header.
Authenticate via basic authentication header:
GET https://cep.example.com/login/basic
Authorization: Basic {base64 of REPO\user1:LDAP_PASSWORD:1:user1_password}
Authorization: Basic {base64 of user1:LDAP_PASSWORD:1:user1_password}
Authorization: Basic {base64 of REPO\user1:PASSWORD:1:user1_password}
Authorization: Basic {base64 of user1:PASSWORD:1:user1_password}
Authorization: Basic {base64 of REPO\user1:EMERG_PASSWORD:1:user1_password}
Authorization: Basic {base64 of user1:EMERG_PASSWORD:1:user1_password}
environment:
- CEP_BASICAUTH_ENABLE=true
environment:
- CEP_BASICAUTH_ENABLE=false
CEP_BASICAUTH_ENFORE_PROXY_REDIRECT¶
If this parameter it true all request to /login will be redirected to /login/basic for basic authentication via authorization header if all the following dependencies fulfilled.
- CEP_BASICAUTH_ENFORE_PROXY_REDIRECT=true
- CEP_BASICAUTH_ENABLE=true
- Request is forwarded by a trusted proxy and X-Forwarded-For is present.
- Authorization header is present
- User is directly requesting /login
environment:
- CEP_BASICAUTH_ENABLE=true
- CEP_BASICAUTH_ENFORE_PROXY_REDIRECT=true
environment:
- CEP_BASICAUTH_ENABLE=false
- CEP_BASICAUTH_ENFORE_PROXY_REDIRECT=false
CEP_BASICAUTH_REQUEST_AUTH¶
If this parameter is enabled, the CEP will ask for username and password via basic authentication If no basic auth header is present. If this feature is not enabled, the user will be redirected to the normal login form.
environment:
- CEP_BASICAUTH_REQUEST_AUTH=true
environment:
- CEP_BASICAUTH_REQUEST_AUTH=false
CEP_ENABLED_LANGUAGES¶
The CEP supports the following languages. They can be enabled by setting this parameter. By default, en and de are enabled. If the user's preferred language is not available the CEP will fall back the configured default language witch can be configured with the CEP_DEFAULT_LANGUAGE parameter.
The CEP support the following languages: Danish (da), Spanish (es), French (fr), Hungarian (hu), Italian (it), Japanese (ja), Dutch (nl), Polish (pl), Portuguese (pt), Russian (ru), Slovenian (sl), Swedish (sv), Chinese (zh), and Traditional Chinese (zh_TW). By default, English (en) and German (de) are enabled.
environment:
- CEP_ENABLED_LANGUAGES=["en", "de", "fr"]
environment:
- CEP_ENABLED_LANGUAGES=["en", "de"]
CEP_ENFORCE_WIZARD¶
If this parameter is enabled, the CEP enforce users to enroll missing methods, configured for the wizard with the parameter with CEP_AAF_WIZARD_METHODS.
environment:
- CEP_ENFORCE_WIZARD=true
environment:
- CEP_ENFORCE_WIZARD=false
CEP_CTE_METHODS¶
List of methods require a call to ensure users have access to the cell phone, email and voice number. If this is enabled for a supported method, the user receives OTP via SMS, VOICE or EMAIL to prove he has access.
Trusted Endpoint Required
The endpoint for the CEP must be a trusted endpoint.
Deprecated
Since AA does support this feature now, this parameter is deprecated and will be removed with 2.0.
environment:
- CEP_CTE_METHODS=["SMS_OTP:1", "EMAIL_OTP:1", "VOICE_OTP:1"]
environment:
- CEP_CTE_METHODS=[]
CEP_CUSTOMIZER_USERS¶
Authorize configured users to access the translation editor and make modifications to the CEP translations.
environment:
- CEP_CUSTOMIZER_USERS=["REPO_NAME\\user1234"]
environment:
- CEP_CUSTOMIZER_USERS=[]
CEP_CUSTOMIZER_GROUPS¶
Authorize users within the configured groups to access the translation editor and make modifications to the CEP translations.
Note
It you use the CEP_CUSTOMIZER_GROUPS parameter is necessary to enable the "Return groups on logon" option in the "Authenticators Management" event. Otherwise, AA will not provide group-related information for the CEP.
environment:
- CEP_CUSTOMIZER_GROUPS=["CN=Grouname,CN=Users,DC=cep,DC=corp"]
environment:
- CEP_CUSTOMIZER_GROUPS=[]
CEP_COMPROMISED_PASSWORD_CHECK¶
If this parameter is enabled, the CEP validates that the given password has not been compromised by checking that it is not included in any of the public data breaches tracked by haveibeenpwned.com. In order to perform the password validation, this constraint doesn't send the raw password value to the service API. Instead, it follows a secure process known as k-anonymity password validation.
Note
Please make sure the CEP is able to connect to the configured endpoint
environment:
- CEP_COMPROMISED_PASSWORD_CHECK=true
environment:
- CEP_COMPROMISED_PASSWORD_CHECK=false
CEP_COMPROMISED_PASSWORD_CHARSET¶
Defines the character set for the compromised password API. The default UTF-8 setting is suitable for most environments.
environment:
- CEP_COMPROMISED_PASSWORD_CHARSET=UTF-8
environment:
- CEP_COMPROMISED_PASSWORD_CHARSET=UTF-8
CEP_COMPROMISED_PASSWORD_ENDPOINT¶
This optional parameter allows the configuration of a custom endpoint from different vendors that support k-anonymity password validation.
environment:
- CEP_COMPROMISED_PASSWORD_ENDPOINT=https://api.vendor.com/range/%s
environment:
- CEP_COMPROMISED_PASSWORD_ENDPOINT=https://api.pwnedpasswords.com/range/%s
CEP_COMPROMISED_PASSWORD_APIKEYHEADER¶
This optional parameter allows the configuration of an authorization header name if required by the vendor's API.
environment:
- CEP_COMPROMISED_PASSWORD_APIKEYHEADER=x-api-auth
environment:
- CEP_COMPROMISED_PASSWORD_APIKEYHEADER=null
CEP_COMPROMISED_PASSWORD_APIKEY¶
This optional parameter allows the configuration of the authorization header value.
environment:
- CEP_COMPROMISED_PASSWORD_APIKEY=secret
environment:
- CEP_COMPROMISED_PASSWORD_APIKEY=null
CEP_DEFAULT_LOGIN_CHAIN¶
These methods will be used if no chain was found to create a fake chain. This can be used to prevent username guessing. If CEP_AAF_EXPOSE_NOCHAIN=true, the user see an error message.
Note
If CEP_AAF_EXPOSE_NOCHAIN=true, the user see an error message.
environment:
- CEP_ALLOWED_FIRST_TIME_METHODS=["PASSWORD:1", "HOTP:1"]
environment:
- CEP_ALLOWED_FIRST_TIME_METHODS=[]
CEP_DEFAULT_LOGIN_METHOD¶
This method will be used if no chain was found to create a fake single method chain. This can be used to prevent username guessing. If CEP_DEFAULT_LOGIN_CHAIN is configured, it will overwrite this parameter with the configured methods.
Note
If CEP_AAF_EXPOSE_NOCHAIN=true, the user see an error message.
environment:
- CEP_DEFAULT_LOGIN_METHOD=LDAP_PASSWORD:1
environment:
- CEP_DEFAULT_LOGIN_METHOD=[]
CEP_DEFAULT_LANGUAGE¶
The CEP supports multiple languages, which can be configured with the CEP_ENABLED_LANGUAGES parameter. The default language will be used If the user's preferred language is not available or not configured as allowed language.
environment:
- CEP_DEFAULT_LANGUAGE=de
environment:
- CEP_DEFAULT_LANGUAGE=en
CEP_DEVICE_NAMES¶
Device names like HOTP-, TOTP-, U2F-, FIDO2-Tokens and Smartphone.
environment:
- 'CEP_DEVICE_NAMES={"de" : {"hotp": "YubiKey", "hotp_plural": "YubiKeys", "totp": "Feitian", "totp_plural": "Feitian", "u2f": "YubiKey", "u2f_plural": "YubiKey", "fido2": "YubiKey 5", "fido2_plural": "YubiKey 5", "smartphone": "Smartphone", "smartphone_plural": "Smartphones"}, "en" : {"hotp": "YubiKey", "hotp_plural": "YubiKeys", "totp": "Feitian", "totp_plural": "Feitian", "u2f": "YubiKey", "u2f_plural": "YubiKey", "fido2": "YubiKey 5", "fido2_plural": "YubiKey 5", "smartphone": "Smartphone", "smartphone_plural": "Smartphones"}}'
environment:
- 'CEP_DEVICE_NAMES={"de" : {"hotp": "HOTP-Token", "hotp_plural": "HOTP-Tokens", "totp": "TOTP-Token", "totp_plural": "TOTP-Tokens", "u2f": "U2F-Token", "u2f_plural": "U2F-Tokens", "fido2": "TOTP-Token", "fido2_plural": "U2F-Tokens", "smartphone": "Smartphone", "smartphone_plural": "Smartphones"}, "de" : {"hotp": "HOTP-Token", "hotp_plural": "HOTP-Tokens", "totp": "TOTP-Token", "totp_plural": "TOTP-Tokens", "u2f": "U2F-Token", "u2f_plural": "U2F-Tokens", "fido2": "TOTP-Token", "fido2_plural": "U2F-Tokens", "smartphone": "Smartphone", "smartphone_plural": "Smartphones"}}'
CEP_DISPLAY_NOTSUPPORTED_METHODS¶
If true not client supported methods will be displayed, but the user cannot enroll or managed. Default: false
environment:
- CEP_DISPLAY_NOTSUPPORTED_METHODS=true
environment:
- CEP_DISPLAY_NOTSUPPORTED_METHODS=false
CEP_ENABLE_FIRST_TIME_MESSAGE¶
If true users will see a first-time user message. The messages can be customized with text and a video.
environment:
- CEP_ENABLE_FIRST_TIME_MESSAGE=true
environment:
- CEP_ENABLE_FIRST_TIME_MESSAGE=false
CEP_ENABLE_LOGIN_MESSAGE_OF_THE_DAY¶
Enables a message of the day above the login form. It can be individual translated by mounting an additional translation file.
Lang phrase is:
controller.login.index.mod: Title of modal window
environment:
- CEP_ENABLE_LOGIN_MESSAGE_OF_THE_DAY=true
environment:
- CEP_ENABLE_LOGIN_MESSAGE_OF_THE_DAY=false
CEP_ENABLE_MESSAGE_OF_THE_DAY¶
Enables a message of the day. Users can hide the massage for the current session.
Lang phareses are:
modal.mod.title: Title of modal window modal.mod.body: Body of modal window
environment:
- CEP_ENABLE_MESSAGE_OF_THE_DAY=true
environment:
- CEP_ENABLE_MESSAGE_OF_THE_DAY=false
CEP_EMAIL_ENABLED¶
If true email notifications are enabled, additional parameters are required. At a minimum, CEP_EMAIL_MAILER_DSN and one event, such as CEP_EMAIL_NOTIFY_ON_LOGIN, are required.
environment:
- CEP_EMAIL_ENABLED=true
environment:
- CEP_EMAIL_ENABLED=false
CEP_EMAIL_MAILER_DSN¶
The DSN of a mail server is used to send notifications. If the username is a fully qualified email address, the "@" sign must be URL encoded.
environment:
- CEP_EMAIL_MAILER_DSN=smtp://user%40example.com:password@mail.example.com:587
environment:
- CEP_EMAIL_MAILER_DSN=
CEP_EMAIL_NOTIFY_ON_LOGIN¶
If configured to true, a notification will be sent to users after they have successfully logged in.
environment:
- CEP_EMAIL_NOTIFY_ON_LOGIN=true
environment:
- CEP_EMAIL_NOTIFY_ON_LOGIN=false
CEP_EMAIL_NOTIFY_ON_ENROLLMENT¶
If configured to true, a notification will be sent to users if a new method has been enrolled.
environment:
- CEP_EMAIL_NOTIFY_ON_ENROLLMENT=true
environment:
- CEP_EMAIL_NOTIFY_ON_ENROLLMENT=false
CEP_EMAIL_NOTIFY_ON_UPDATE¶
If configured to true, a notification will be sent to users if a method has been updated.
environment:
- CEP_EMAIL_NOTIFY_ON_UPDATE=true
environment:
- CEP_EMAIL_NOTIFY_ON_UPDATE=false
CEP_EMAIL_NOTIFY_ON_DELETE¶
If configured to true, a notification will be sent to users if a method has been deleted.
environment:
- CEP_EMAIL_NOTIFY_ON_DELETE=true
environment:
- CEP_EMAIL_NOTIFY_ON_DELETE=false
CEP_EMAIL_SENDER_ADDR¶
Sender address of all notification emails
environment:
- CEP_EMAIL_SENDER_ADDR=user@example.com
environment:
- CEP_EMAIL_SENDER_ADDR=
CEP_EMAIL_SENDER_NAME¶
Name of sender
environment:
- CEP_EMAIL_SENDER_NAME=Sender Name
environment:
- CEP_EMAIL_SENDER_NAME=
CEP_EMAIL_SMIME_CRT¶
SMIME Certificate to sign notifications emails.
environment:
- CEP_EMAIL_SMIME_CRT=/some/path/within/the/conatiner/cert.pem
environment:
- CEP_EMAIL_SMIME_CRT=
CEP_EMAIL_SMIME_KEY¶
The private key is used for SMIME signatures. If the key is encrypted, CEP_EMAIL_SMIME_PASSWORD must be configured.
environment:
- CEP_EMAIL_SMIME_KEY=/some/path/within/the/conatiner/key.pem
environment:
- CEP_EMAIL_SMIME_KEY=
CEP_EMAIL_SMIME_PASSWORD¶
Secret password to decrypt the PEM encoded private key.
environment:
- CEP_EMAIL_SMIME_PASSWORD=secret
environment:
- CEP_EMAIL_SMIME_PASSWORD=
CEP_ENABLE_NATIVE_U2F¶
If true, the browser's native U2F implementation is used instead of the devices service. Beware of restrictions the APPID and Facets.
environment:
- CEP_ENABLE_NATIVE_U2F=true
environment:
- CEP_ENABLE_NATIVE_U2F=false
CEP_FIDO2_AUTHENTICATOR_ATTACHMENT¶
This parameter enforces the authenticator attachment of WebAuthn / FIDO2 attestation. It can be configured for cross-platform and platform. Cross-platform are typically roaming authenticators which can be used on different clients.
environment:
- CEP_FIDO2_AUTHENTICATOR_ATTACHMENT=cross-platform
environment:
- CEP_FIDO2_AUTHENTICATOR_ATTACHMENT=
CEP_FIDO2_AAGUID_BLACKLIST¶
This parameter enable the configuration of a blacklist for prohibited AAGIUDs that users are not allowed to enroll.
environment:
- CEP_FIDO2_AAGUID_BLACKLIST=["a25342c0-3cdc-4414-8e46-f4807fca511c"]
environment:
- CEP_FIDO2_AAGUID_BLACKLIST=[]
CEP_FIDO2_AAGUID_WHITELIST¶
This parameter allow for the configuration of a whitelist for AAGIUDs that users are permitted to enroll in. By default, all AAGIUDs are allowed.
environment:
- CEP_FIDO2_AAGUID_WHITELIST=["a25342c0-3cdc-4414-8e46-f4807fca511c"]
environment:
- CEP_FIDO2_AAGUID_WHITELIST=[]
CEP_FIDO2_ADDITIONAL_SECURITY_CHECK¶
This parameter enables additional security checks on the FIDO MDS database. These checks include validation of the certificate chain and status messages related to critical security issues.
Note
The CEP requires HTTPS access to the following hosts for this feature: secure.globalsign.com, crl.globalsign.com and mds.fidoalliance.org
environment:
- CEP_FIDO2_ADDITIONAL_SECURITY_CHECK=true
environment:
- CEP_FIDO2_ADDITIONAL_SECURITY_CHECK=false
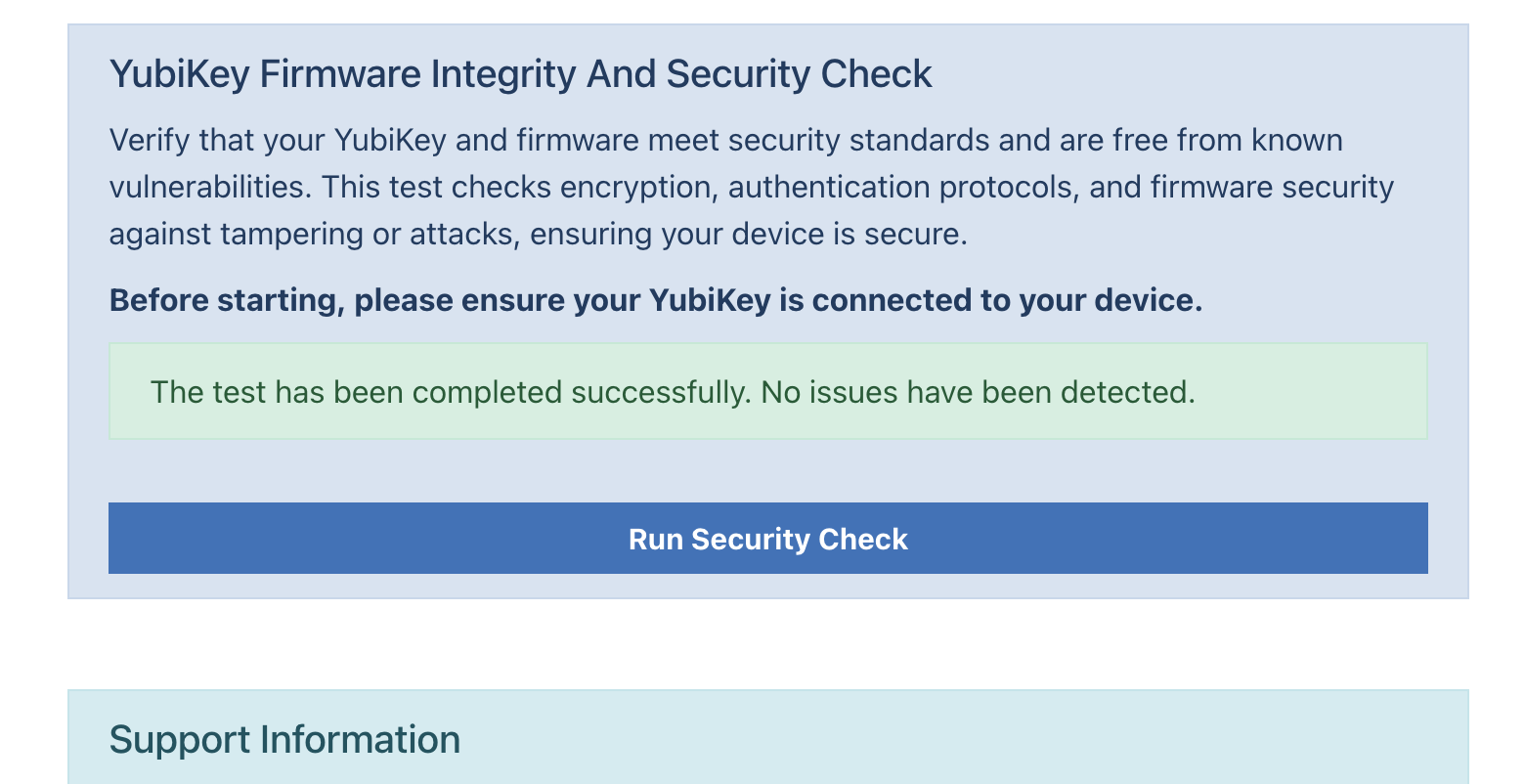
CEP_FIDO2_SHOW_SECURITY_CHECK¶
If this parameter is set to true, an additional security check will be displayed. The user must already be logged in to use this test. This test performs the same checks configured for enrollments.
environment:
- CEP_FIDO2_SHOW_SECURITY_CHECK=true
environment:
- CEP_FIDO2_SHOW_SECURITY_CHECK=false
CEP_FIDO2_USE_DOMAIN¶
If true, the domain of the FQHN will always be used for the enrollment for FIDO2. This is the best practice to make users enrollments available under every FQHN under this domain.
environment:
- CEP_FIDO2_USE_DOMAIN=false
environment:
- CEP_FIDO2_USE_DOMAIN=true
CEP_FIDO2_PUBLIC_SUFFIX_ONLY¶
The FIDO2 specification mandates the use of public DNS suffixes for the RP_ID. This parameter enables the option to bypass public suffix verification, thereby permitting the use of local domain names.
Browser Vendors May Discontinue Support in the Future.
We cannot assure universal compatibility across all browser platforms. Browser vendors may also decide to eliminate the capability of using local domain names in the future. In such a scenario, all users will need to re-enroll with a new public suffix domain name.
environment:
- CEP_FIDO2_PUBLIC_SUFFIX_ONLY=false
environment:
- CEP_FIDO2_PUBLIC_SUFFIX_ONLY=true
CEP_FIDO2_REQUIRE_KEY_PROTECTION_HARDWARE¶
This parameter should be set true If the authenticator must have hardware-based key management.
environment:
- CEP_FIDO2_REQUIRE_KEY_PROTECTION_HARDWARE=true
environment:
- CEP_FIDO2_REQUIRE_KEY_PROTECTION_HARDWARE=false
CEP_FIDO2_REQUIRE_KEY_PROTECTION_SECURE_ELEMENT¶
This parameter should be set true If the authenticator must have secure element for key management.
environment:
- CEP_FIDO2_REQUIRE_KEY_PROTECTION_SECURE_ELEMENT=true
environment:
- CEP_FIDO2_REQUIRE_KEY_PROTECTION_SECURE_ELEMENT=false
CEP_FIDO2_REQUIRE_MATCHER_PROTECTION_ON_CHIP¶
This parameter should be set true If the authenticator's matcher must run on the chip.
environment:
- CEP_FIDO2_REQUIRE_MATCHER_PROTECTION_ON_CHIP=true
environment:
- CEP_FIDO2_REQUIRE_MATCHER_PROTECTION_ON_CHIP=false
CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_EXTERNAL¶
This parameter should be set true If the authenticator must be hardware-based, that it is removable or remote from the FIDO user device.
environment:
- CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_EXTERNAL=true
environment:
- CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_EXTERNAL=false
CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_WIRED¶
This parameter should be set true If the external authenticator must have an exclusive wired connection, e.g. through USB, firewire or similar. Please keep in mind, some authenticator support multiple connection types.
environment:
- CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_WIRED=true
environment:
- CEP_FIDO2_REQUIRE_ATTACHMENT_HINT_WIRED=false
CEP_FIDO2_REQUIRE_VENDOR_CERTIFICATE¶
If this parameter is configured true the CEP will check allowed vendor root CA's. If the chain could not be validated the CEP will deny the enrollment.
environment:
- CEP_FIDO2_REQUIRE_VENDOR_CERTIFICATE=true
environment:
- CEP_FIDO2_REQUIRE_VENDOR_CERTIFICATE=false
CEP_FIDO2_REQUIRE_SERIAL_NUMBER¶
If this parameter is configured true the CEP necessitates the entry of a serial number for a FIDO2 authenticator.
environment:
- CEP_FIDO2_REQUIRE_SERIAL_NUMBER=true
environment:
- CEP_FIDO2_REQUIRE_SERIAL_NUMBER=false
CEP_HIDDEN_METHODS¶
YAML array of the methods a user will not see in authenticators overview.
environment:
- CEP_HIDDEN_METHODS=["EMERG_PASSWORD:1", "WEBAUTH:1", "EMAIL_OTP:1"]
environment:
- CEP_HIDDEN_METHODS=[]
CEP_HIDE_AASERVER_INFORMATION¶
This parameter controls information disclosure of AA server information on the support page. It is disabled by default.
environment:
- CEP_HIDE_AASERVER_INFORMATION=false
environment:
- CEP_HIDE_AASERVER_INFORMATION=true
CEP_HIDE_INFO_PAGE¶
If this parameter is true support / information page will not be displayed
environment:
- CEP_HIDE_INFO_PAGE=true
environment:
- CEP_HIDE_INFO_PAGE=false
CEP_HIDE_INFO_PAGE_UNAUTHENTICATED¶
Info page will be hidden to unauthenticated users If parameter is true.
environment:
- CEP_HIDE_INFO_PAGE_UNAUTHENTICATED=true
environment:
- CEP_HIDE_INFO_PAGE_UNAUTHENTICATED=false
CEP_HIDE_VERSION¶
If this parameter is true support / information page will not be displayed
environment:
- CEP_HIDE_VERSION=true
environment:
- CEP_HIDE_VERSION=false
CEP_HOTP_SERIAL_ALGORITHM¶
Set the algorithm for hotp serial automatic completion detection.
environment:
- CEP_HOTP_SERIAL_ALGORITHM=yubikey
environment:
- CEP_HOTP_SERIAL_ALGORITHM=yubikey
CEP_HOTP_SERIAL_AUTOMATIC¶
Enables or disables the automatic form flow for OTP token enrollment.
environment:
- CEP_HOTP_SERIAL_AUTOMATIC=false
environment:
- CEP_HOTP_SERIAL_AUTOMATIC=true
CEP_HOTP_SERIAL_LEN¶
Length of HOTP token serial numbers for completion detection of serial number input.
environment:
- CEP_HOTP_SERIAL_LEN=12
environment:
- CEP_HOTP_SERIAL_LEN=7
CEP_HOTP_SERIAL_NUMERIC¶
If set to false, automatic completion detection for serial number input accepts alphanumeric serial numbers.
Note
If you're using devices with serial numbers longer than 14 digits, you must set this parameter to false.
environment:
- CEP_HOTP_SERIAL_NUMERIC=false
environment:
- CEP_HOTP_SERIAL_NUMERIC=true
CEP_INFO_VERSION_LINK¶
If this parameter is true version number tuned into hyperlink for info page.
environment:
- CEP_INFO_VERSION_LINK=true
environment:
- CEP_INFO_VERSION_LINK=false
CEP_LDAP_CHANGE_AS_USER¶
If configured true user must enter the current and the new password to change it. The CEP then use the old password with users DN to authenticate against the LDAP server to be able to change the current password to the new password. If configured false the CEP use SSPR to reset the password using the configured binddn and bindpw of the directory configuration, configured via CEP_LDAP_DIRECTORIES parameter.
environment:
- CEP_LDAP_CHANGE_AS_USER=false
environment:
- CEP_LDAP_CHANGE_AS_USER=true
CEP_LDAP_DIRECTORIES¶
Directory configuration for each repository configured in AA. UNIQUE_REPOSITORY_NAME must match with the name configured in AA for this repository.
Directory Types
The following types are supported: ld = LDAP, ed = edirectory, ad = Microsoft Active Directory
User base
If userbase is configured, CEP use it to build the userDN. %s will be replaced by the username of the logged-in to create a valid userDN. If no userbase is configured, CEP use the userDN provided by AA API.
Note
If the hosts element is configured dnsdomain will always be ignored and no autodiscovery will be take place.
environment:
- CEP_LDAP_ENABLE=true
- 'CEP_LDAP_DIRECTORIES={"UNIQUE_REPOSITORY_NAME" : {"type": "ld", "hosts": ["ldap.example.com"], "port": 389, "tls": true, "version": 3, "timeout": 5, "binddn": "cn=admin,dc=company,dc=com", "bindpw": "PaSSWord1", "userbase": "cn=%s,ou=Users,dc=company,dc=com", "basedn": "dc=company,dc=com"}, "MSAD" : {"type": "ad", "hosts": ["dc1.cep.corp"], "port": 636, "ssl": true, "version": 3, "timeout": 5, "userbase": "CN=%s,OU=Users,DC=cep,DC=corp", "basedn": "DC=cep,DC=corp"}}'
You can also configure auto-discovery by removing the hosts and adding dnsdomain element. The optional parameter site allows you to limit the query to a specific site. Please note the CEP will query _ldaps.tcp.example.com If SSL is enabled and _ldap.tcp.example.com If SSL is disabled.
environment:
- CEP_LDAP_ENABLE=true
- 'CEP_LDAP_DIRECTORIES={"UNIQUE_REPOSITORY_NAME" : "MSAD" : {"type": "ad", "dnsdomain": "cep.corp", "site": "test", "ssl": true, "version": 3, "timeout": 5, "binddn": "adadmin1@cep.corp", "bindpw": "PaSSWord1", "userbase": "CN=%s,OU=Users,DC=cep,DC=corp", "basedn": "DC=cep,DC=corp"}}'
The following example is a minimal configuration for Active Directory. The user must input his current password which is then used for user authentication.
environment:
- CEP_LDAP_ENABLE=true
- 'CEP_LDAP_DIRECTORIES={"UNIQUE_REPOSITORY_NAME" : {"type": "ad", "ssl": true, "dnsdomain": "cep.corp", "userbase": "CN=%s,OU=Users,DC=cep,DC=corp", "basedn": "DC=cep,DC=corp"}}'
The next example enables SSPR using service account credentials for LDAP binding to reset users password.
environment:
- CEP_LDAP_ENABLE=true
- 'CEP_LDAP_DIRECTORIES={"UNIQUE_REPOSITORY_NAME" : {"type": "ad", "ssl": true, "dnsdomain": "cep.corp", "userbase": "CN=%s,OU=Users,DC=cep,DC=corp", "binddn": "adadmin1@cep.corp", "bindpw": "PaSSWord1", "basedn": "DC=cep,DC=corp"}}'
- CEP_LDAP_CHANGE_AS_USER=false
environment:
- CEP_LDAP_ENABLE=false
- CEP_LDAP_DIRECTORIES=[]
CEP_LDAP_ENABLE¶
If this variable set to true LDAP component for ldao repository passwors will be enabled.
environment:
- CEP_LDAP_ENABLE=true
environment:
- CEP_LDAP_ENABLE=false
CEP_LDAP_LEADING_REPO¶
Define the name of leading repository. If a user found in the leading repository, the LDAP password will only be changed in the leading repository. If no leading repository is configured, users password will be changed in the repository presented by advanced authentication API.
Be are of warm body's
Please make sure users in repository "A" are the same users as in repository "B". Otherwise, users of repository "A" can modify the passwords of users in repository "B"
environment:
- CEP_LDAP_LEADING_REPO=NAME_OF_REPOSITORY
environment:
- CEP_LDAP_LEADING_REPO=
CEP_LDAP_UNLOCK_EVENT¶
Individual event used to unlock AD user accounts should exclusively grant access to users from an active directory repository. For this event the option "Bypass user lockout in repository" must be enabled via AA event configuration.
environment:
- CEP_LDAP_UNLOCK_EVENT=AdUserUnlock
environment:
- CEP_LDAP_UNLOCK_EVENT=
CEP_LDAP_PASSWORD_COMPLEX¶
If true some numeric password which are easy to guess are no longer accepted for the LDAP_PASSWORD:1 method.
environment:
- CEP_LDAP_PASSWORD_COMPLEX=false
environment:
- CEP_LDAP_PASSWORD_COMPLEX=true
CEP_LDAP_PASSWORD_READONLY¶
If Logon with expired password is set to "Ask to change" on "Authenticators Management" event and this parameter set to false CEP will present a form to change users password during the logon. It also enables modification of the directory password in method details. Direct LDAP configuration will be prioritized method details.
environment:
- CEP_LDAP_PASSWORD_READONLY=false
environment:
- CEP_LDAP_PASSWORD_READONLY=true
CEP_LDAP_PASSWORD_MAX_LEN¶
Maximum length of LDAP password. This should be the same as repositories password policy.
environment:
- CEP_LDAP_PASSWORD_MAX_LEN=10
environment:
- CEP_LDAP_PASSWORD_MAX_LEN=99999
CEP_LDAP_PASSWORD_MIN_LEN¶
Minimum length of LDAP password. This should be the same as repositories password policy.
environment:
- CEP_LDAP_PASSWORD_MIN_LEN=10
environment:
- CEP_LDAP_PASSWORD_MIN_LEN=6
CEP_LDAP_PASSWORD_POLICY¶
If true, the user's password must be compliant with his individual personal or group password policy configured within your directory.
environment:
- CEP_LDAP_PASSWORD_POLICY=true
environment:
- CEP_LDAP_PASSWORD_POLICY=false
CEP_LDAP_PASSWORD_REGEX¶
Regular expression to check the compatibility LDAP password. If CEP_LDAP_PASSWORD_POLICY is enabled this parameter will be ignored.
environment:
- CEP_LDAP_PASSWORD_REGEX=/^(?=.*[0-9])(?=.*[a-z])(?=\S*[\d]).{10,}$$/i
environment:
- CEP_LDAP_PASSWORD_REGEX=/^(?=.*[0-9])(?=.*[a-z])(?=\S*[\d]).{6,}$$/i
CEP_LINK_IMPRINT¶
URL to imprint. If set link will be displayed in the footer.
environment:
- CEP_LINK_IMPRINT=https://example.com/imprint.html
environment:
- CEP_LINK_IMPRINT=
CEP_LINK_LIST_FOOTER¶
Array of footer links displayed in the page footer. If the required language was not found the CEP use the default language. In Most cases, this will be "en". Therefore, "en" should always be configured as language for footer links.
environment:
- 'CEP_LINK_LIST_FOOTER={"de" : {"Anleitungen" : "https://example.com"}, "en" : {"Howto" : "https://example.com"}}'
environment:
- CEP_LINK_LIST_FOOTER=[]
CEP_LINK_LOGIN_VIDEOTUTORIAL¶
URL of a video tutorial. The link will be on the login screen below the portal description.
environment:
- CEP_LINK_LOGIN_VIDEOTUTORIAL=http://youtube.com
environment:
- CEP_LINK_LOGIN_VIDEOTUTORIAL=
CEP_LINK_LOSTPASSWORD¶
Link to reset user's password. If set link will be displayed below login from.
environment:
- CEP_LINK_LOSTPASSWORD=https://example.com/password/reset.html
environment:
- CEP_LINK_LOSTPASSWORD=
CEP_LINK_OBJECT_VIDEOTUTORIAL¶
URL for an embedded video. The video will be displayed below the use case view.
environment:
- CEP_LINK_OBJECT_VIDEOTUTORIAL=https://www.youtube.com/embed/W7qWa52k-nE
environment:
- CEP_LINK_OBJECT_VIDEOTUTORIAL=
CEP_LINK_PRIVACY¶
URL to the privacy terms. If set link will be displayed in the footer.
environment:
- CEP_LINK_PRIVACY=https://example.com/privacy.html
environment:
- CEP_LINK_PRIVACY=
CEP_LINK_SUPPORT¶
URL to support website. If set link will be displayed in the footer.
environment:
- CEP_LINK_SUPPORT=https://example.com/suppoer.html
environment:
- CEP_LINK_SUPPORT=
CEP_LINK_TERMS¶
URL to the terms of use. If set link will be displayed in the footer.
environment:
- CEP_LINK_TERMS=https://example.com/terms.html
environment:
- CEP_LINK_TERMS=
CEP_LINK_VIDEOTUTORIAL¶
URL of a video tutorial. The link will be displayed below the destruction of authenticator overview.
environment:
- CEP_LINK_VIDEOTUTORIAL=http://youtube.com
environment:
- CEP_LINK_VIDEOTUTORIAL=
CEP_METHOD_BLUETOOTH_ENABLE_WIZARD¶
If true user will see a small wizard of how to configure / pair his BT devices.
environment:
- CEP_METHOD_BLUETOOTH_ENABLE_WIZARD=true
!! info "Default"
environment:
- CEP_METHOD_BLUETOOTH_ENABLE_WIZARD=false
CEP_METHOD_EMAIL_AUTOENROLL¶
This parameter controls auto enrollment of EMAIL_OTP:1 method. If enabled the method will be auto enrolled if not present.
environment:
- CEP_METHOD_EMAIL_AUTOENROLL=true
environment:
- CEP_METHOD_EMAIL_AUTOENROLL=false
CEP_METHOD_NAMES_FROM_AAF¶
If true method names configured in AAF will be used in the CEP.
environment:
- CEP_METHOD_NAMES_FROM_AAF=false
environment:
- CEP_METHOD_NAMES_FROM_AAF=true
CEP_METHOD_PASSWORD_MAX_LEN¶
Maximum length of the password for the PASSWORD:1 method.
environment:
- CEP_METHOD_PASSWORD_MAX_LEN=8
environment:
- CEP_METHOD_PASSWORD_MAX_LEN=99999
CEP_METHOD_PASSWORD_MIN_LEN¶
Minimum length of password for the PASSWORD:1 method. The CEP utilizes the endpoint policy for determining the minimum length of PASSWORD:1 by default.
environment:
- CEP_METHOD_PASSWORD_MIN_LEN=8
environment:
- CEP_METHOD_PASSWORD_MIN_LEN=0
CEP_METHOD_PASSWORD_REGEX¶
Regular expression for password (PASSWORD:1) complexity validation.
environment:
- CEP_METHOD_PASSWORD_MIN_LEN=4
- CEP_METHOD_PASSWORD_MAX_LEN=4
- CEP_PASSWORD_COMPLEX_NUMERIC=true
- CEP_METHOD_PASSWORD_REGEX=/^[0-9]*$$/i
environment:
- CEP_METHOD_PASSWORD_MIN_LEN=5
- CEP_METHOD_PASSWORD_MAX_LEN=999999
- CEP_PASSWORD_COMPLEX_NUMERIC=false
- CEP_METHOD_PASSWORD_REGEX=/^(?=.*[0-9])(?=.*[a-z])(?=\S*[\d]).*$$/i
CEP_METHOD_SMARTPHONE_APP_LINKS¶
This parameter configures download links for the smartphone push app.
environment:
- 'CEP_METHOD_SMARTPHONE_APP_LINKS={"NetIQ": {"ios":"https://apps.apple.com/de/app/netiq-advanced-authentication/id843545585", "android":"https://play.google.com/store/apps/details?id=com.netiq.oathtoken"}, {"MyAuth": {"ios":"https://apps.apple.com/de/app/XYZ/XYZ", "android":"https://play.google.com/store/apps/details?id=XYZ"}}'
environment:
- 'CEP_METHOD_SMARTPHONE_APP_LINKS={"NetIQ": {"ios":"https://apps.apple.com/de/app/netiq-advanced-authentication/id843545585", "android":"https://play.google.com/store/apps/details?id=com.netiq.oathtoken"}}'
CEP_METHOD_SMARTPHONE_APP_VENDOR_ICON¶
This parameter configures the icon of the vendor app. TO make the icon available it must be mounted into the container via volume. It is possible to store the container in your custom CEP container image. In that case no extra volume will be required. If no icon or name configured via parameter, CEP use the default NetIQ icon and display the configured vendor from AA without any modification.
volumes:
./app-icon-myauth.png:/var/www/html/public/build/app-icon-myauth.png
environment:
- 'CEP_METHOD_SMARTPHONE_APP_VENDOR_ICON={"NetIQ": "app-icon-NetIQ.png", "MyAuth": "app-icon-myauth.png"}'
environment:
- 'CEP_METHOD_SMARTPHONE_APP_VENDOR_ICON={"NetIQ": "app-icon-NetIQ.png"}'
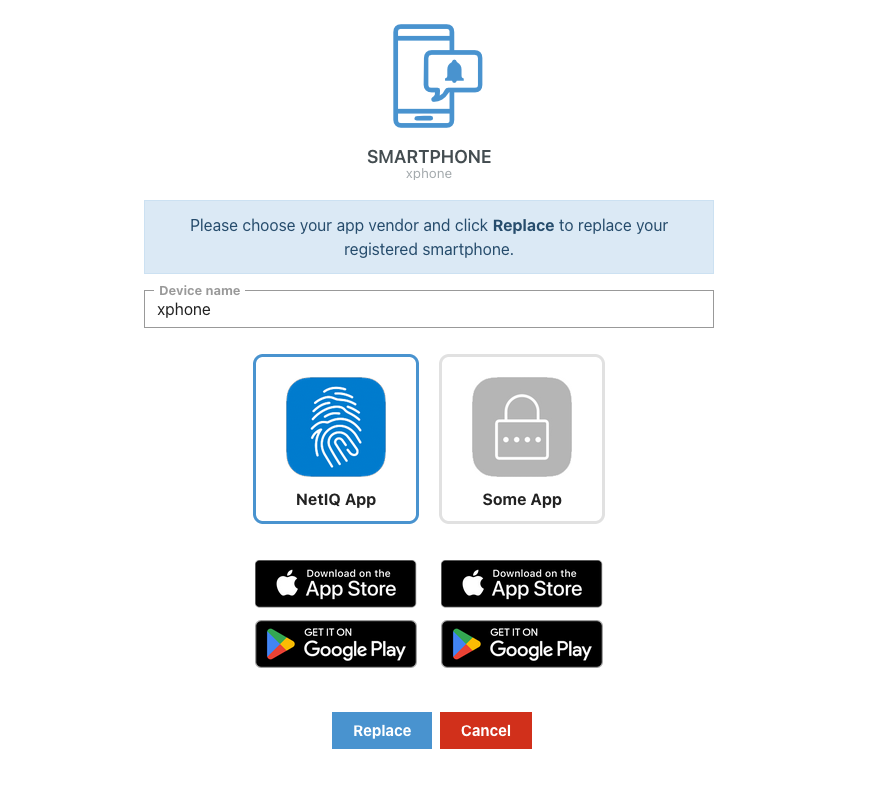
CEP_METHOD_SMARTPHONE_APP_VENDOR_LABEL¶
The CEP provides selection of smartphone app vendor.
In this example MyAuth is the configured app vendor. AA configuration and array keys for label and icons must match exactly.
environment:
- 'CEP_METHOD_SMARTPHONE_APP_VENDOR_LABEL={"NetIQ": "NetIQ Auth", "MyAuth": "My Auth"}'
environment:
- 'CEP_METHOD_SMARTPHONE_APP_VENDOR_LABEL={"NetIQ": "NetIQ Auth"}'
CEP_METHOD_SMARTPHONE_ENABLE_WIZARD¶
If true user will see a small wizard of how to install the NetIQ Smartphone app.
environment:
- CEP_METHOD_SMARTPHONE_ENABLE_WIZARD=true
environment:
- CEP_METHOD_SMARTPHONE_ENABLE_WIZARD=false
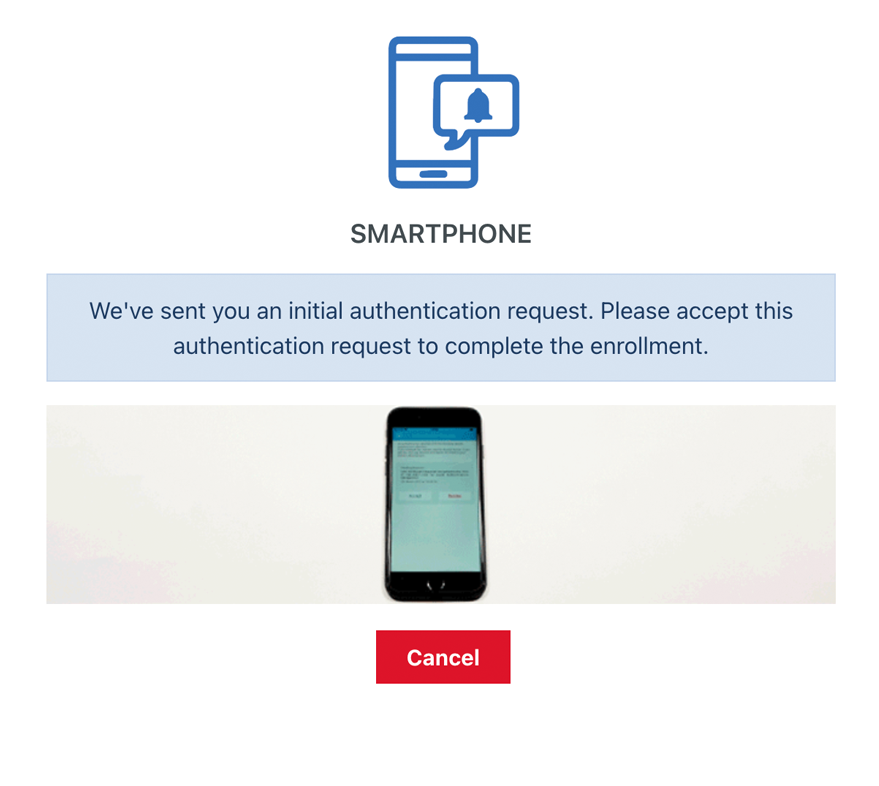
CEP_METHOD_SMARTPHONE_ENFORCE_TEST¶
If configured true, an initial authentication test will be started to complete the smartphone enrollment.
environment:
- CEP_METHOD_SMARTPHONE_ENFORCE_TEST=true
environment:
- CEP_METHOD_SMARTPHONE_ENFORCE_TEST=false
CEP_METHOD_SMARTPHONE_WIZARD_OS¶
With this parameter, the smartphone OS can be switched to iOS, android or both.
environment:
- CEP_METHOD_SMARTPHONE_WIZARD_OS=["ios"]
environment:
- CEP_METHOD_SMARTPHONE_WIZARD_OS=["ios", "android"]
CEP_METHOD_SORT_ALPHANUMERIC¶
This parameter enables alphanumeric sorting of enrolled methods and available methods on authenticators overview. If alphanumeric sorting disabled the CEP sort enrolled methods in order coming from AA and CEP configuration.
environment:
- CEP_METHOD_SORT_ALPHANUMERIC=true
environment:
- CEP_METHOD_SORT_ALPHANUMERIC=false
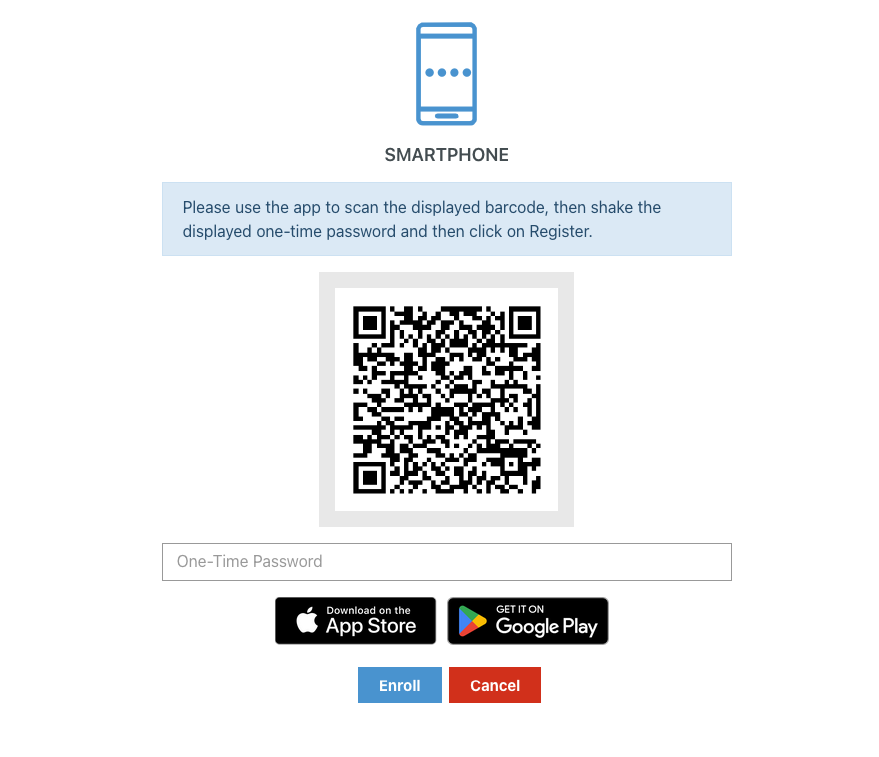
CEP_METHOD_TOTP_APP_LINKS¶
This parameter configures download links for the TOTP smartphone app.
environment:
- 'CEP_METHOD_TOTP_APP_LINKS={"ios":"https://apps.apple.com/de/app/google-authenticator/id388497605", "android":"https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2"}'
environment:
- CEP_METHOD_TOTP_APP_LINKS=
CEP_METHOD_WINHELLO_ENFORCE_NETBIOSNAME¶
If configured true CEP will use login session username (NETBIOS-Name with domain prefix) on Windows Hello enrollment for on AD users.
environment:
- CEP_METHOD_WINHELLO_ENFORCE_NETBIOSNAME=true
environment:
- CEP_METHOD_WINHELLO_ENFORCE_NETBIOSNAME=false
CEP_METHOD_WINHELLO_HIDE_DEVICENAME¶
If configured true users will not see input filed for device name on Windows Hello enrollment view.
environment:
- CEP_METHOD_WINHELLO_HIDE_DEVICENAME=true
environment:
- CEP_METHOD_WINHELLO_HIDE_DEVICENAME=false
CEP_METHOD_WINHELLO_REQUIRE_DEVICENAME¶
If configured true user must enter in addition a device names of his PC to enroll Windows Hello.
environment:
- CEP_METHOD_WINHELLO_REQUIRE_DEVICENAME=true
environment:
- CEP_METHOD_WINHELLO_REQUIRE_DEVICENAME=false
CEP_METHOD_WINHELLO_SHOW_IMPROVE¶
If false improved face recognition for windows hello will be disabled in the wizard. Default: true
environment:
- CEP_METHOD_WINHELLO_SHOW_IMPROVE=true
environment:
- CEP_METHOD_WINHELLO_SHOW_IMPROVE=false
CEP_PASSWORD_COMPLEX_NUMERIC¶
If true some numeric pins that are easy to guess are no longer accepted by the CEO for the PASSWORD:1 method.
CEP_REMOTE_AUDITLOG_FACILITY¶
Log facility for remote audit logging.
environment:
- CEP_REMOTE_AUDITLOG_FACILITY=audit
environment:
- CEP_REMOTE_AUDITLOG_FACILITY=user
CEP_PERFORMANCE_MAX_CLIENTS¶
This parameter controls the maximum number of active client connections the CEP will handle. Consider increasing this value if your system has sufficient memory and the CEP is operating under high-load scenarios.
Each active user session can consume up to 150–180 MB of memory, depending on the workload and application behavior.
environment:
- CEP_PERFORMANCE_MAX_CLIENTS=100
environment:
- CEP_PERFORMANCE_MAX_CLIENTS=40
CEP_REMOTE_AUDITLOG_HOST¶
Hostname or IP-Address for remote audit logging.
environment:
- CEP_REMOTE_AUDITLOG_HOST=192.168.100.100
environment:
- CEP_REMOTE_AUDITLOG_HOST=
CEP_REMOTE_AUDITLOG_IDENT¶
Identififer of the CEP for log messages.
environment:
- CEP_REMOTE_AUDITLOG_IDENT=app123
environment:
- CEP_REMOTE_AUDITLOG_IDENT=cep
CEP_REMOTE_AUDITLOG_LEVEL¶
Log level for remote audit logging. If error is configured, the CEP will only log failed authentications. Log level info includes all enrollment events, deletion of a method and all authentication related user activities.
environment:
- CEP_REMOTE_AUDITLOG_LEVEL=ERROR
environment:
- CEP_REMOTE_AUDITLOG_LEVEL=INFO
CEP_REMOTE_AUDITLOG_PORT¶
UDP port number for remote audit logging.
environment:
- CEP_REMOTE_AUDITLOG_PORT=1024
environment:
- CEP_REMOTE_AUDITLOG_PORT=514
CEP_RETURNURL_DEFAULT_LABLE¶
Parameter to set the default label which will be used If no label set by query string parameter.
environment:
- CEP_RETURNURL_DEFAULT_LABLE=myparam1
environment:
- CEP_RETURNURL_DEFAULT_LABLE=
CEP_RETURNURL_ENABLE¶
If enabled, return URLs are enabled and used during the logout of a user. The label is the key element of a URL list. URLs of this list will be used to return a user to a specific URL. List of URLs can be configured with CEP_RETURNURL_LABLE parameter. The parameter can be used on any URL of the CEP.
Info
The parameters are is case sensitive.
GET https://cep.example.com/login?returnlabel=myparam1
environment:
- CEP_RETURNURL_ENABLE=true
environment:
- CEP_RETURNURL_ENABLE=false
CEP_RETURNURL_LABLE¶
List of return URLs a user will be redirected to after a successful logout.
environment:
- 'CEP_RETURNURL_LABLE={ "myparam1": "https://my1.example.com", "myparam2": "https://my2.example.mom" }'
environment:
- CEP_RETURNURL_LABLE=
CEP_RETURNURL_LABLE_NAME¶
List of names used to change the verbiage of the logout link.
environment:
- 'CEP_RETURNURL_LABLE_NAME={"myparam1": "Go bach to my1.example.com", "myparam2": "Go bach to my2.example.com"}'
environment:
- CEP_RETURNURL_LABLE=
CEP_RETURNURL_SESSION_TIMEOUT¶
If the session timed out or the user has no session on the CEP, the CEP tries to redirect the user back to the return URL instead of the default CEP login.
environment:
- CEP_RETURNURL_SESSION_TIMEOUT=true
environment:
- CEP_RETURNURL_SESSION_TIMEOUT=false
CEP_SECURITY_HTTP_HEADER¶
If enabled the CEP will add the following headers to HTTP responses.
Content-Security-Policy: frame-ancestors 'none'
Strict-Transport-Security: max-age=31536000; includeSubdomains; preload
X-Content-Type-Options: nosniff
X-Frame-Options: deny
environment:
- CEP_SECURITY_HTTP_HEADER=true
environment:
- CEP_SECURITY_HTTP_HEADER=false
CEP_SHOW_ALWAYS_LOGIN_LINKS¶
If disabled, CEP will not display links below the login after the user has entered his username and can select method or chains.
environment:
- CEP_SHOW_ALWAYS_LOGIN_LINKS=false
environment:
- CEP_SHOW_ALWAYS_LOGIN_LINKS=true
CEP_SECURITY_HTTP_HEADER¶
If enabled the CEP will add the following headers to HTTP responses.
Content-Security-Policy: frame-ancestors 'none'
Strict-Transport-Security: max-age=31536000; includeSubdomains; preload
X-Content-Type-Options: nosniff
X-Frame-Options: deny
environment:
- CEP_SECURITY_HTTP_HEADER=true
environment:
- CEP_SECURITY_HTTP_HEADER=false
CEP_SHOW_BIOKEY_FIDO2_WINDOWS_WIZARD¶
Enables a wizard for Biometric key registration for FIDO2.
environment:
- CEP_SHOW_BIOKEY_FIDO2_WINDOWS_WIZARD=true
environment:
- CEP_SHOW_BIOKEY_FIDO2_WINDOWS_WIZARD=false
CEP_SHOW_BIOKEY_U2F_WINDOWS_WIZARD¶
Enables a wizard for Biometric key registration for U2f.
environment:
- CEP_SHOW_BIOKEY_U2F_WINDOWS_WIZARD=true
environment:
- CEP_SHOW_BIOKEY_U2F_WINDOWS_WIZARD=false
CEP_SHOW_LOGIN_CANCEL¶
This parameter enables a cancel button on the login page. If the user click in this link, logon process will be destroyed and the user can start over again.
environment:
- CEP_SHOW_LOGIN_CANCEL=true
environment:
- CEP_SHOW_LOGIN_CANCEL=false
CEP_SHOW_REPOSITORY¶
Boolean value used to determine whether the name of the repository should be displayed before the user logs in.
environment:
- CEP_SHOW_REPOSITORY=true
environment:
- CEP_SHOW_REPOSITORY=false
CEP_SHOW_REPOSITORY_ONLY_FOR¶
Array list of repository names displayed next to the username in the upper-right corner.
environment:
- CEP_SHOW_REPOSITORY_ONLY_FOR=["LDAP", "AD1234]
environment:
- CEP_SHOW_REPOSITORY_ONLY_FOR=[]
CEP_SHOW_USECASE_INFO¶
If true additional information will be displayed above the use cases.
environment:
- CEP_SHOW_USECASE_INFO=true
environment:
- CEP_SHOW_USECASE_INFO=false
CEP_SINGLE_ALLOWD_METHOD¶
Array of methods allowed for registration only if this is the one and only method the user has enrolled.
environment:
- CEP_SINGLE_ALLOWD_METHOD=["EMAIL_OTP:1"]
environment:
- CEP_SINGLE_ALLOWD_METHOD=[]
CEP_SINGLE_METHOD_CHAINS¶
If false, an error message will be displayed if the chain is successfully logged on that only has one method. This can be used to prevent some users from logging onto the CEP via an external network with just one factor.
environment:
- CEP_SINGLE_METHOD_CHAINS=false
environment:
- CEP_SINGLE_METHOD_CHAINS=true
CEP_SINGLE_METHOD_CHAINS_REGEX¶
Regular expression on the username which, if matches the regular expression, it is impossible for a user to log in with a chain that contains only method.
environment:
- CEP_SINGLE_METHOD_CHAINS_REGEX=/^test[0-9]*$$/i
environment:
- CEP_SINGLE_METHOD_CHAINS_REGEX=/^.*$$/i
CEP_SINGLE_METHOD_CHAINS_REGEX_REPO¶
If true the name of the repository is also used to check the regular expression.
environment:
- CEP_SINGLE_METHOD_CHAINS_REGEX_REPO=true
- CEP_SINGLE_METHOD_CHAINS_REGEX=/^ldap\\test[0-9]*$$/i
environment:
- CEP_SINGLE_METHOD_CHAINS_REGEX=/^.*$$/i
CEP_SINGLE_METHOD_CHAINS_VERBOSE¶
If true and CEP_SINGLE_METHOD_CHAINS false, an error message will be displayed if the user tries to log in with only one method. If false, a message is displayed when logging in that a login is only possible with multi-factor.
environment:
- CEP_SINGLE_METHOD_CHAINS_VERBOSE=true
environment:
- CEP_SINGLE_METHOD_CHAINS_VERBOSE=false
CEP_SSO_OAUTH2_ATTRIBUTES_URL¶
OAUTH2 attributes url
environment:
- CEP_SSO_OAUTH2_ATTRIBUTES_URL=/osp/a/TOP/auth/oauth2/getattributes
environment:
- CEP_SSO_OAUTH2_GRANT_URL=/osp/a/TOP/auth/oauth2/getattributes
CEP_SSO_OAUTH2_CLIENT_ID¶
OAUTH2 client ID
environment:
- CEP_SSO_OAUTH2_CLIENT_ID=76931daaa7c7f134531e7938b3a9052c
environment:
- CEP_SSO_OAUTH2_CLIENT_ID=
CEP_SSO_OAUTH2_CLIENT_SECRET¶
OAUTH2 client secret
environment:
- CEP_SSO_OAUTH2_CLIENT_SECRET=93143b935897d93143b935897d632afda25db5ff2036c25db5ff2036c
environment:
- CEP_SSO_OAUTH2_CLIENT_SECRET=
CEP_SSO_OAUTH2_ENABLE¶
If true SSO via OAUTH2 is enabled to replace the portal logon.
environment:
- CEP_SSO_OAUTH2_ENABLE=true
environment:
- CEP_SSO_OAUTH2_ENABLE=false
CEP_SSO_OAUTH2_GRANT_URL¶
OAUTH2 grant url
environment:
- CEP_SSO_OAUTH2_GRANT_URL=/osp/a/TOP/auth/oauth2/grant
environment:
- CEP_SSO_OAUTH2_GRANT_URL=/osp/a/TOP/auth/oauth2/grant
CEP_SSO_OAUTH2_LOGOUT_URL¶
URL to logout a user
environment:
- CEP_SSO_OAUTH2_LOGOUT_URL=/osp/a/TOP/auth/oauth2/logout
environment:
- CEP_SSO_OAUTH2_LOGOUT_URL=/osp/a/TOP/auth/oauth2/logout
CEP_SSO_WEBAUTH_AUTOENROLL¶
This parameter auto enrollment of WEBAUTH:1 after login. If the user logged in, can enroll WEBAUTH:1 as an authentication method, enrollment start automatically and the user will be redirected to the IDP and back into the overview of the CEP. CEP will use this default IDP (CEP_SSO_WEBAUTH_DEFAULT_IDP) if configured. Alternatively, the CEP use the first IDP configured in AA.
environment:
- CEP_SSO_WEBAUTH_AUTOENROLL=true
- CEP_SSO_WEBAUTH_DEFAULT_IDP=IDP_NAME_IN_AA_CONFIG
environment:
- CEP_SSO_WEBAUTH_AUTOENROLL=false
- CEP_SSO_WEBAUTH_DEFAULT_IDP=IDP_NAME_IN_AA_CONFIG
CEP_SSO_WEBAUTH_DEFAULT_IDP¶
The CEP use the first IDP for enrollment. If another IDP should be selected, configuration by this parameter is necessary. The name must identical with in AA configured IDP name.
environment:
- CEP_SSO_WEBAUTH_DEFAULT_IDP=_some_idp_name
environment:
- CEP_SSO_WEBAUTH_DEFAULT_IDP=null
CEP_SSO_WEBAUTH_ENABLE¶
This parameter enables SSO via WEBAUTH:1 method.
environment:
- CEP_SSO_WEBAUTH_ENABLE=true
environment:
- CEP_SSO_WEBAUTH_ENABLE=false
CEP_SSO_WEBAUTH_LOGOUT_URL¶
A URL the user will be redirected to after successful logout. If no URL is configured, the User login via WEBAUTH:1 again. If CEP_RETURNURL_LABLE is configured, CEP prioritize the configured CEP_RETURNURL_LABLE for final redirection after logout.
environment:
- CEP_SSO_WEBAUTH_LOGOUT_URL=https://sso.example.com/logout
environment:
- CEP_SSO_WEBAUTH_LOGOUT_URL=null
CEP_SSO_WEBAUTH_USERNAME_COOKIE¶
Cookie name to re-identify user for webauth:1 authentication process creation. If this cookie is not found, users' must enter their username.
environment:
- CEP_SSO_WEBAUTH_USERNAME_COOKIE=_some_cookie_name
environment:
- CEP_SSO_WEBAUTH_USERNAME_COOKIE=username
CEP_TOTP_DISABLE_HARDWARE_TOKEN¶
If this parameter is enabled, no hardware token registration is allowed.
environment:
- CEP_TOTP_DISABLE_HARDWARE_TOKEN=true
environment:
- CEP_TOTP_DISABLE_HARDWARE_TOKEN=false
CEP_TOTP_ISSUER¶
Name of issuer for TOTP secrets displayed in Google Authenticator. Google Authenticator format of QR code (Key URI) in AA method must be enabled to individualize the issuer.
environment:
- CEP_TOTP_ISSUER=CompanyName
environment:
- CEP_TOTP_ISSUER=
CEP_TOTP_SEED_CLIPBOARD¶
Enabling this parameter allows the user to manually copy the TOTP seed to the clipboard for easy pasting into their authenticator app.
environment:
- CEP_TOTP_SEED_CLIPBOARD=true
environment:
- CEP_TOTP_SEED_CLIPBOARD=false
CEP_TOTP_LABEL_WITH_REPO¶
If this parameter is enabled, the username displayed in Google Authenticator includes the repository name (REPOSITORY/username).
environment:
- CEP_TOTP_LABEL_WITH_REPO=true
environment:
- CEP_TOTP_LABEL_WITH_REPO=false
CEP_TRUSTED_HEALTHCHECK_IPS¶
The CEP provide a health check URL (/health) for monitoring. This URL can only be accessed by trusted clients. This parameter allowed to configure the trusted client IP addresses. The IP address :1 and 127.0.0.1 are always trusted. Untrusted clients can check the cached result of the last health check via /health/status. For information go to the feature page.
If the /health request comes from a trusted proxy, the X-Forwarded-For header overwrite the client IP address. The IP address of the proxy servers must be configured by CEP_AAF_TRUSTED_PROXIES parameter.
environment:
- CEP_TRUSTED_HEALTHCHECK_IPS=["192.168.100.100", 192.168.1.0/24"]
environment:
- CEP_TRUSTED_HEALTHCHECK_IPS=[]
CEP_VENDOR_CARD_READER¶
Vendor name of RFID card reader to choose call to action images.
environment:
- CEP_VENDOR_CARD_READER=hid
environment:
- CEP_VENDOR_CARD_READER=hid
CEP_VENDOR_HOTPTOKEN¶
Vendor name of HOTP tokens to choose call to action images. You can choose between: feitian, yubikey5c, swissbit and yubikey
environment:
- CEP_VENDOR_HOTPTOKEN=yubikey
environment:
- CEP_VENDOR_HOTPTOKEN=yubikey
HTTP_PROXY¶
An HTTP proxy server that is used for all API-related requests. It is highly recommended to configure CEP_HTTP_PROXY and CEP_HTTPS_PROXY.
environment:
- HTTP_PROXY=http://user:password@server:8080
environment:
- HTTP_PROXY=
HTTPS_PROXY¶
An HTTPS proxy server that is used for all API-related requests. It is highly recommended to configure CEP_HTTPS_PROXY and CEP_HTTP_PROXY.
environment:
- HTTPS_PROXY=https://user:password@server:8080
environment:
- HTTPS_PROXY=
NO_PROXY¶
Comma- or space-separated list of machine or domain names, with optional :port part. If no :port part is present, it applies to all ports on that domain.
environment:
- NO_PROXY=localhost,host.example.com
environment:
- NO_PROXY=localhost